There’s this trick going around on Discord recently where if you send any GIF
from Tenor, and then type s/e/x, then it turns it into a different meme GIF.
Here’s how it works.
The sed syntax
For operating systems based on Unix or Linux, there’s usually a simple terminal
command included called sed, which is most commonly used to
run text replacement commands. Here’s a very simple example of what a basic
sed command looks like:
consoleCopy
|
|
Discord likely implemented this in order to appeal to IRC1 users. Since IRC doesn’t support editing messages, it’s common for people to send messages in that format to tell people about changes to their previous message. Discord implemented this into both their web/desktop client and their iOS app, excluding the Android app.
Note that while real sed commands can get much more complicated, Discord’s
implementation doesn’t support those advanced features2.
SEE ALSO: Text substitution in Discord using sed
What does s/e/x do?
When you send a GIF using the GIF picker on Discord, it actually sends the link to the GIF, which is served by Tenor. For example, here’s a GIF sent from Tenor:
https://tenor.com/view/cat-massage-gif-24282757
Running s/e/x will take the first occurrence of e and replace it with x.
The link becomes the following (notice the bolded letter x):
https://txnor.com/view/cat-massage-gif-24282757
Then, all that’s left to do is to buy the domain txnor.com, and write a simple
program to run on it. In fact, it looks like that domain was purchased purely in
order to make this trick possible3.
How does it display on Discord without redirecting?
When viewing any of the URLs on txnor.com in a normal web browser, you get
redirected to a tweet. However, Discord is able to display the
image without being redirected.
When Discord loads a website to generate an embed, it uses a user agent4 (which is a little piece of text which tells the server what your browser is) which looks something like this:
textCopy
|
|
The important part here is the word Discord. If you visit the website with
your user agent set to anything containing Discord
(case-insensitive)5, then it serves the image directly.
Default image
If you go to any URL on txnor.com that doesn’t fit one of the existing
patterns/games, then it returns this fallback image:
txnor.com
Extra features
Double sex
If you then run s/e/x a second time, then it changes to a different image:

s/e/x a second time.
This works in a simple way as well. The next e that appears in the URL is
inside /view/. So, after typing s/e/x a second time, the URL becomes:
https://txnor.com/vixw/cat-massage-gif-24282757
Chess (s/w/ag)
Another cool feature is that you can play chess by typing s/w/ag after typing
the initial message of s/e/x.
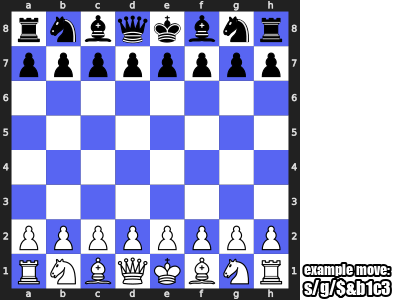
s/w/ag after having done s/e/x.
s/w/ord
If you do s/w/ord after s/e/x, then it starts a fighting game (titled
“Wumpagotchi Adventures”. You can use three commands: s/d/dATK,
s/d/dDEF, and s/d/dHUG.
Here are a few example images:
Main s/w/ord screen
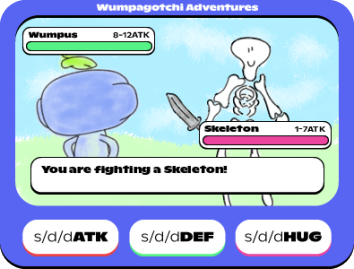
s/w/ord after having done s/e/x.
ATK command
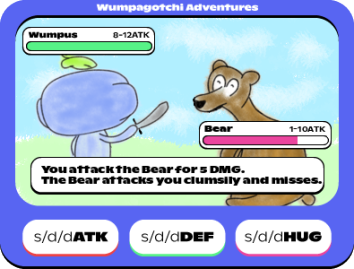
s/d/dATK
DEF command
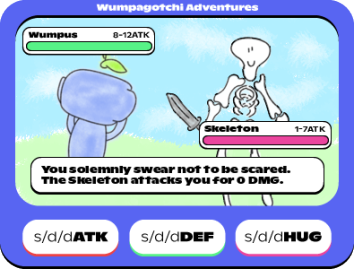
s/d/dDEF
HUG command
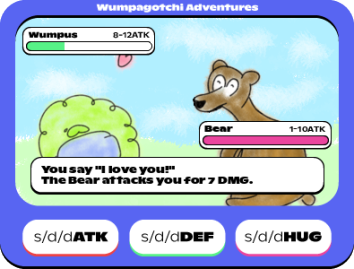
s/d/dHUG
Win screen
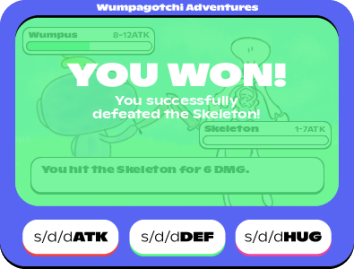
s/w/ord game.
Lose screen
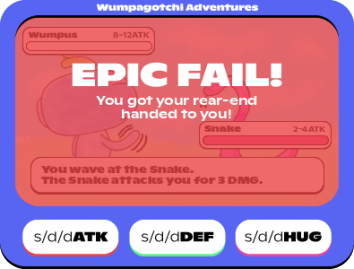
s/w/ord game.
6969th Discord Sexer
If you happen to get a one in 6970 chance, it will instead return a special image:
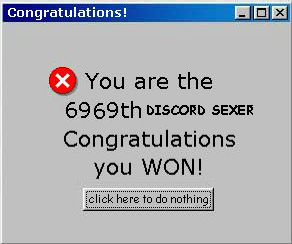
Here’s a snippet of the code that handles this chance:
pythonCopy
|
|
I believe it’s supposed to be a 1/6969 chance, but random.randint in Python
includes both numbers. That means that the possible numbers that it could pick
would be 0, 1, … 6968, 6969. If you were to count the numbers included in that
sequence, it would total 6970.
Math challenge
Any URL that matches this regular expression will
instead return a randomized math challenge. This means the URL can be
https://txnor.com/ followed by either math, math_challenge, or
mathchallenge, a single optional slash, and then any text that’s made up of
only letters, numbers, underscores or hyphens.
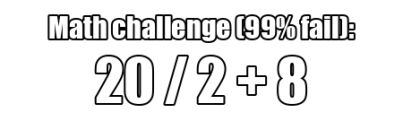
What’s special is that the math challenge is set to not be cached. That means that it should6 give everyone a different question.
How it works is that when each person’s Discord client sends a request to the Discord CDN to get the image, the client caches that image. That means each client will see the same challenge problem, even if the user restarts the client. But separate clients will not have it cached, so they’ll request it again themselves, and different numbers will be generated.
Discord sex is open source
Thanks to a comment from Rebane on this post, I now know that the
server running on txnor.com is open source. See
rebane2001/txnor-server.
YouTube video
Rebane also made a YouTube video about this trick. Make sure to check it out too!
-
IRC (Internet Relay Chat) is a simple text-based chat system. It’s a very old protocol, however its simplicity and minimalism is the main reason people choose it. It’s not very popular anymore. ↩︎
-
Also note that in Discord’s implementation, the trailing slash (after
goodbye) can be ommitted (making it justs/hello/goodbye), but with the realsedcommand, it’s required. ↩︎ -
According to a quick WHOIS lookup, the domain was registered on May 3, 2022. That’s the same day that @Rebane tweeted about the new feature (
going to https://txnor.com redirects to this tweetnow the domain redirects to Rebane’s YouTube video about the hack), so I assume that this is the only reason they bought the domain. ↩︎ -
If you actually care, there’s a Wikipedia article, and a page on WhatIsMyIPAddress.com which also explain what a user agent is. ↩︎
-
According to the source code, it looks like
Intel Mac OS X 11.6; rv:92.0also triggers the same response. ↩︎ -
The caching behavior seems to be inconsistent, so sometimes it does end up giving multiple people the same question. ↩︎
Comments
If you provide an email address, you can enable notifications for replies to your comment. It will not be shown publicly.